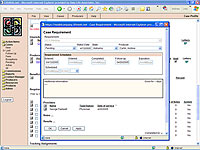
The Lifeweb system was developed to meet the specific needs of companies and their associated distribution channels. This case management system focuses on a high level of automation for the policy issue process to rapidly disseminate and retrieve information. This ultimately improves regulatory compliance, communication, and collaboration with the producers and producer groups. The Lifeweb system seamlessly integrates producers, underwriters, reinsurers, and home office support staff via the web. Lifeweb allows 24x7 access both onshore and offshore.
|
|
 |
  |
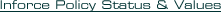
The current status of all the business written, including policy values is available through a link to either the carrier's legacy system or a TPA.
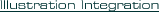
The system provides options for using a Data Life developed web-based illustration system or the ability to exchange data with other illustration systems.
|
Action items may be associated with a case, a producer, a client or general items without a specific association. Each action item may be assigned to members of the workgroup or to the producers and assigned a priority. Based upon rules established by the workgroup, action items or email notes can be automatically generated by the system to reflect changes in the status of a case.

Producer license and contract status is either maintained on the system or may be linked to the carrier's legacy system. The system supports complex reporting hierarchies with separate contracting hierarchies for variable business.
|
|

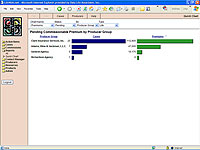
Reports and graphs are available to provide assistance to the support staff as well as to provide management information on workflow, productivity and production.
The security in the system has been designed to allow only authorized user access to the data about clients, policies, and producers. Even individual members of the staff can be restricted from sensitive data such as commission information and confidential client information.
|
 |
The data security involves full encryption of the data stream using Secure Sockets Layer (SSL), so that there is no vulnerability to data-packet interception. |
|
|